Why is website security so important?
Personal data protection and GDPR compliance
In the era of GDPR, personal data protection has become not only a legal requirement, but also an expectation from users. Websites collect and process huge amounts of personal data, from email addresses to financial information. Negligence in security may lead to the leakage of this data, which in turn may result in serious legal and financial consequences for both website owners and their users.
The impact of security on credibility and SEO
The security of a website has a direct impact on its positioning in search engines and user perception. Google and other search engines favor secure sites by using protocols such as HTTPS as one of their ranking factors. A site that is deemed unsafe may be lowered in search results, impacting visibility, site traffic, and ultimately business success.
Risks of unsecured sites
Unsecured websites are exposed to a number of threats, such as data theft, hacker attacks, malware and phishing. These attacks can lead not only to financial losses, but also to loss of trust and reputation in the eyes of customers. Especially for online businesses, where customer trust is crucial, protection against such threats is essential.
In summary, website security is essential to protect data, maintain user trust, comply with legal regulations, and maintain ranking in search results. In the following sections, we will look at specific threats and methods for securing websites to ensure they are as protected as possible.
What threats is the website exposed to?
Data theft and its consequences
What is Data Theft?
Data theft refers to unauthorized access and theft of sensitive information from a website. This may include users' personal data, financial information, passwords, credit card details and even confidential company data. Attackers can use various techniques, such as phishing, password brute force attacks, software exploits, and SQL injection, to gain access to protected resources.
Consequences of Data Theft
The effects of data theft can be far-reaching for both website owners and users:
- Loss of trust: Loss of customer data can lead to serious damage to a company's reputation and loss of user trust.
- Legal consequences: Data security breaches can result in serious legal consequences, including financial penalties, especially in the context of regulations such as GDPR.
- Financial losses: Leakage of personal data or credit card information can lead to financial losses for both users and companies.
- Use of data for criminal purposes: The stolen data can be used for further fraud, e.g. identity theft.
Threats related to Session Hijacking
What is Session Hijack?
Session hijacking, also known as session hijacking, is another serious threat in the world of website security. This is a technique in which an attacker takes control of a user's session, which can lead to unauthorized access to sensitive data or site features.
Session hijacking occurs when an attacker gains access to a user's unique session identifier (often called a session token), which is used to communicate with the server. An attacker can hijack a session through a variety of methods, such as intercepting unencrypted network traffic, exploiting web application vulnerabilities, and other techniques such as phishing and man-in-the-middle attacks.
Consequences of Session Hijacking
- Loss of Privacy: Session hijacking can lead to the leak of confidential user information such as personal data, financial information or account details.
- Unauthorized Access: An attacker can use a hijacked session to gain access to protected areas of the website, which can lead to a number of dangers, including manipulation of user data.
Malicious Redirects and their impact on users
What are Malicious Redirects?
Malicious redirects are a technique in which a website user is unexpectedly redirected to another website, usually containing malware or fake content. Such redirects may be the result of hacking attacks, in which cybercriminals inject malicious code into the website, changing its behavior. They can also occur by exploiting vulnerabilities in plugins or content management platforms (CMS).
Impact of Malicious Redirects on Users
- Security risk: Redirecting to malicious sites can expose users to malware, ransomware, or phishing, which could lead to the theft of personal or financial information.
- Disruption of user experience: Unexpected redirects can disrupt and discourage users, leading to higher bounce rates and lower engagement.
SEO spamming
SEO spamming, also known as "SEO spam" or "black-hat SEO", is a technique used by people trying to fraudulently boost a website's rankings in search results. This practice negatively affects the quality and credibility of the website and can lead to long-term damage to the perception of the website by search engines and users.
How does SEO Spamming work?
SEO spamming often includes activities such as injecting unwanted keywords or links into a page, creating fake pages, or hiding text and links. Attackers can exploit site vulnerabilities to add malicious code or unauthorized content that manipulates search engine algorithms to undeservedly increase a site's visibility in search results.
The effects of SEO spamming on the website
- Lower rankings: Search engines like Google penalize sites that use SEO spamming techniques, which can result in a significant drop in search rankings.
- Removal from search results: In extreme cases, pages may be completely removed from the search engine index, resulting in their invisibility in search results.
DDoS attacks
DDoS (Distributed Denial of Service) attacks are one of the most destructive threats to websites. They involve flooding a website with huge amounts of network traffic, which exceeds its processing capacity and leads to temporary or long-term disabling of services.
Characteristics of DDoS Attacks
These attacks use numerous compromised computer systems (often botnets) to generate massive amounts of traffic directed at a single website. They differ from simple DoS attacks in that they come from many different sources, making them difficult to block. They can take many forms, from simple attacks that overload the server to more complex strategies that exploit specific weaknesses in the server or application configuration.
Consequences of DDoS Attacks
- Page availability interruptions: DDoS attacks can effectively render a website inaccessible, meaning users and customers cannot use it.
- Financial losses: Website interruptions can lead to direct financial losses, especially for companies selling online or offering digital services.
Consequences of being placed on the Black List
Getting blacklisted by search engines or anti-spam services is a serious problem for website owners. This means that the website has been classified as dangerous or contains malware.
The effects of being placed on the Black List
- Reduced search engine visibility: Blacklisted sites may be excluded from search results, significantly reducing their visibility.
- User warnings: Many web browsers and antivirus programs warn users against visiting blacklisted sites, which may result in a drop in traffic on the site.
- Long-term reputational effects: The process of removing a site from a blacklist can be long and complicated, and the mere presence on the site can have a long-term impact on user trust.
Defacement - Changing the appearance of the website by hackers
Defacement, i.e. changing the appearance of a website by hackers, is a type of attack that involves unauthorized modification of the appearance of a website. This type of attack is often used by hackers to convey a specific message, protest, or simply to demonstrate a weakness in a site's security.
Characteristics of a Defacement Attack
- Altering page content: During a defacement attack, hackers replace the original page content with their own messages, images, or HTML code. These changes may be visible to all visitors to the website.
- Purpose of attack: Often, such attacks are intended to draw attention to a specific political or social issue, but they can also be an act of digital vandalism without a deeper message.
Ransomware - What is it?
Ransomware is a type of malware that locks access to a computer system or data, demanding a ransom from the victim to unlock it. Ransomware has become one of the biggest threats in cybersecurity.
Ransomware mechanism of action
- Data encryption: Most often, ransomware encrypts data on the attacked device, making it impossible to access it without a special key that is offered in exchange for paying a ransom.
- Ransom demand: Victims are forced to pay a ransom, often in cryptocurrency, to regain access to their data.
Effects of a Ransomware Attack
- Data Loss: If the ransom is not paid, your data may be lost permanently.
- Significant Financial Losses: The costs associated with a ransomware attack can include not only the ransom, but also losses related to business downtime.
- Reputational and legal consequences: Ransomware attacks can lead to long-term damage to a company's reputation and potential legal consequences related to a data breach.
Cross-Site Scripting (XSS) - What does it involve?
Cross-site scripting (XSS) is a type of cyber attack in which attackers inject malicious script into the content of a website. This script is then executed by the user's browser, which can lead to various unwanted effects.
Characteristics of an XSS Attack
- Vulnerability Exploitation: XSS attacks often exploit vulnerabilities in web applications, allowing malicious JavaScript code to be injected into the page.
- Types of XSS Attacks: There are different types of XSS attacks, including persistent (where code is stored on the server), reflected (where code is reflected from the server to the user), and DOM-based (manipulating the DOM environment of the page).
Consequences of an XSS Attack
- Data theft: XSS attacks can lead to the theft of data such as user cookies and session tokens.
- Extraction of confidential information: By injecting scripts, hackers can extract confidential information from website users.
SQL and Code Injections
SQL Injection
- Attack Mechanism: SQL Injection attacks involve injecting malicious SQL commands through forms on a website, which allows for database manipulation.
- Impact: Such attacks may lead to unauthorized access to data, modification, deletion or even destruction of the database.
Code Injection
- Attack Mechanism: Code Injection attacks involve injecting and executing malicious code in an application, which may lead to taking control of the application or server.
- Impact: Possible consequences include data theft, malware infections, and significant site disruptions.
Additionally, it should be remembered that each such attack also affects the credibility of the brand. For companies that focus mainly on acquiring new customers, this will most likely only result in financial losses, while companies that focus on long-term work may unfortunately disappear from the market.
In the case of safety, the same rule applies as in the case of health: "Prevention is better than cure." That's why there's an extensive section below describing various ways to protect yourself from attacks. However, we must remember that we will never be 100% safe, but we can make hacking us unprofitable.
How to effectively secure your website?
Port Blocking as a Protection Measure
Port blocking is a key part of securing websites. This method works by restricting access to specific network ports through which the server communicates, which helps prevent unauthorized access and attacks.
How to Block Ports
- Identifying Unnecessary Ports: The first step is to identify the ports that are not needed for your website or application to function. Any unnecessarily open port is a potential threat.
- Firewall Configuration: Use a firewall to block all ports that are not needed. The firewall can be configured at the server, network or even application level.
- Applying the Minimum Opening Principle: Apply the minimum port opening principle open only those ports that are absolutely necessary for the operation of your site and its functions.
Tools and practices
- Use of UTM or IDS/IPS: Unified Threat Management (UTM) or Intrusion Detection/Suppression Systems (IDS/IPS) solutions often offer advanced port management capabilities.
- Regular port scanning: Use port scanning tools regularly to ensure that no unauthorized ports have been opened.
- Use secure protocols: Make sure the communication protocols you use (such as SSH, FTPS, TLS/SSL) are secure and up to date.
Protection against DDoS attacks
Protection against DDoS (Distributed Denial of Service) attacks is necessary to maintain business continuity and security of websites. DDoS attacks involve flooding a website with huge amounts of network traffic, which may lead to its complete immobilization.
Methods of protection against DDoS attacks
- Distributed Protection: Using distributed protection systems such as CDN (Content Delivery Networks) that can disperse traffic and reduce its impact on a single point in the network.
- Advanced Detection Systems: Implement real-time DDoS detection and mitigation systems that can quickly respond to unexpected traffic spikes.
- Bandwidth Throttling: Limiting data transfer rates at the server or network level can help manage unexpected traffic increases.
Tools and practices
- Use of firewalls: Configure firewalls to block unnecessary traffic and filter suspicious requests.
- Regular testing and simulations: Conduct regular DDoS attack testing and simulations to assess system readiness and identify areas for improvement.
- Using external services: Collaboration with service providers specializing in DDoS protection who offer advanced solutions and support.
SSH security - Certificates or Keys instead of password
SSH (Secure Shell) is a protocol used for secure communication with the server. Traditionally, SSH access is secured using a username and password, but this method can be vulnerable to brute-force or phishing attacks. A much more secure alternative is to use SSH keys and certificates.
Implementation of SSH Keys
- SSH Key Generation: The first step is to generate an SSH key pair, consisting of a public and private key. The private key is kept securely by the user, while the public key is placed on the server.
- Using a Key instead of a Password: Once configured, access to the SSH server requires the appropriate private key, eliminating the need for a password.
Benefits of using SSH Keys
- Increased security: SSH keys are much harder to crack than traditional passwords. Thanks to their use, the risk of unauthorized access to the server is significantly reduced.
- Protection against Brute-Force Attacks: SSH keys are resistant to password guessing attacks, which are a common problem with traditional authentication methods.
Connection encryption - HSTS and not just HTTPS
HTTPS encryption is the foundation of a secure internet connection. It uses the SSL/TLS protocol to encrypt data sent between the user and the server, preventing it from being intercepted and read by unauthorized persons.
Implementing HSTS (HTTP Strict Transport Security)
- An additional layer of security: HSTS is a security policy that forces all future connections to a given domain to use HTTPS. This prevents man-in-the-middle attacks that can occur when a user first connects to a site over an insecure HTTP connection.
- HSTS Configuration: To implement HSTS, you must add the appropriate HTTP header to the server response. This causes browsers to automatically use a secure HTTPS connection whenever they try to connect to a website.
Benefits of using HSTS
- Automatic Redirect to HTTPS: Users are automatically redirected to a secure version of the site, even if they enter an address with "http".
- Spoofing Attack Protection: HSTS helps protect against spoofing attacks.
Checking the vulnerabilities of CMS plugins and used plugins
Plugins and CMS plug-ins are often a core element of website functionality, but they can also pose a serious security risk if they are not regularly updated and checked for vulnerabilities.
Regular Updates and Monitoring
- Updating Plugins and Plugins: Regular updates are essential because developers often release security patches to protect against newly discovered vulnerabilities.
- Using Vulnerability Scanning Tools: There are many tools, both paid and free, that can automatically scan and report known vulnerabilities in installed plugins and plug-ins.
Limiting the Number of Additives Used
The fewer external additions, the lower the risk of vulnerability. You should avoid installing unnecessary plugins, and update and audit those used regularly.
Restricting Administrative Access
Ensuring that only trusted and responsible users have access to manage plug-ins and plug-ins reduces the risk of unauthorized changes or installation of malicious software.
Web Application Firewall - First Line of Defense
WAF web application firewall monitors and filters traffic coming to the web application, protecting it against malicious requests and attacks such as cross-site scripting (XSS) and SQL injection.
Configuration and Use of WAF
- Choosing the Right WAF Solution: There are many WAF solutions, both hardware-based and cloud-based. It is important to choose one that best suits the needs and architecture of a given website.
- Rule Customization: WAF allows you to create custom rules and policies that can be tailored to a site's specific threats or business requirements.
WAF Monitoring and Updating
- Constant Monitoring: Actively monitoring and analyzing network traffic with WAF allows you to quickly detect and respond to potential threats.
- Regular Updates: To ensure the effectiveness of your WAF, it is important to update its databases and rules regularly to respond to the latest threats and attack techniques.
Secure Headers - Securing headers
Properly configured security headers can prevent many attacks, including clickjacking, XSS, and other script-based vulnerabilities.
Secure Headers implementation
- Strict-Transport-Security (HSTS): Prevents man-in-the-middle attacks by forcing an encrypted HTTPS connection.
- Content-Security-Policy (CSP): Helps prevent XSS attacks by controlling the resources that can be loaded and executed on the page.
- X-Content-Type-Options: Prevents MIME type sniffing attempts that may lead to files being misinterpreted.
- X-Frame-Options: Protection against clickjacking attacks by blocking the possibility of placing the page in a frame.
Headline Monitoring and Testing
- Regular Configuration Reviews: Systematically review and test header configurations to ensure they are up to date and effectively protect against new types of attacks.
- Using Testing Tools: There are online tools and scanners that can help you evaluate and improve your security header configurations.
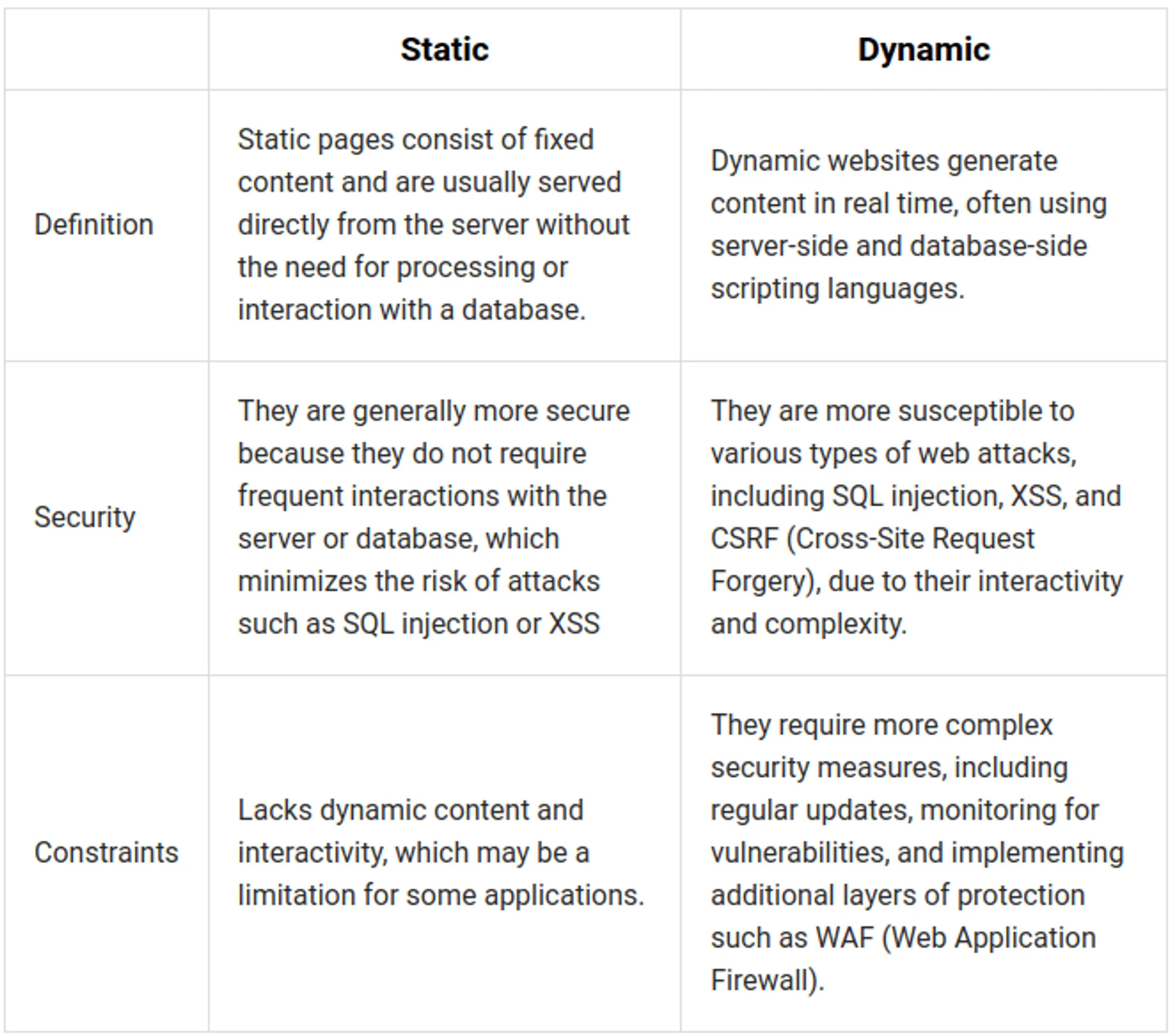
Static vs. Dynamic Pages in the Context of Security
The security of websites can vary significantly depending on whether they are static or dynamic. Each of these types of sites has its own unique security challenges and benefits.
Are the right tools and configuration everything?
Of course not, but you should remember that they contribute a lot to your sense of security. Security is a process, a constant game of cat and mouse with the attacker. You can't buy a security bucket, but you can implement a security policy to help you stay protected.
Security policy
A security policy is a comprehensive set of guidelines and procedures designed to protect an organization's digital assets. In addition to the definition of employee standards and training, it also includes a number of other key elements:
Definition of Standards
- Rules for Creating Passwords: Determining requirements regarding the complexity and frequency of password changes.
- Data Access Management: Establishing procedures for controlling access to sensitive data, including managing user permissions.
- Device Security: Implementing security policies for company devices, including disk encryption and anti-theft.
Staff training
- Developing Security Awareness: Educating employees about digital threats, phishing, and other tactics used by cybercriminals.
- Practical Workshops and Training: Organizing regular practical training, including simulations of phishing attacks, so that employees can better recognize and respond to threats.
Audit and Policy Review
- Regular Security Policy Reviews: Conducting regular audits to identify vulnerabilities and update the policy in line with the latest threats.
- Regulatory Compliance: Ensuring that security policies comply with local and international data protection regulations.
Incident Response Procedures
- Security Incident Response Plan: Developing detailed procedures for responding to security breaches, including internal and external communications.
- Post-Incident Analysis: Conducting an in-depth analysis after each incident to identify causes and make necessary policy changes.
Integration with Business Processes
- Integrating Security into Business Processes: Ensuring that all business processes incorporate security aspects from the beginning of design.
- Communication and Interdepartmental Cooperation: Building a safety culture through cooperation between various departments of the company.
Creating and implementing an effective security policy requires continuous commitment and adaptation to the evolving cyber threat landscape. It is not only a set of procedures, but also a dynamic process that must be updated regularly to effectively protect an organization's digital assets.
In addition, remember to:
- regular security scans
- responsible software updates
- considering hiding access to the CMS behind a private network (VPN)
- providing access to the CMS and server only to the necessary persons
- not storing important and confidential information on the server
Applying these practices allows you to create a solid, multi-layered defense against digital threats, taking your website's security to a higher level. However, we know that there was a lot of information in this article, even though it is an introductory post. However, it is impossible to explain the issue of security on the Internet in even the smallest detail on one page.
How and why is it worth checking a website's history?
Understanding a site's past history, including changes in content, ownership, and updates, can provide valuable clues about potential threats such as past data leaks, hacking attacks, and unauthorized content changes. Here's how you can do it effectively using tools optimized for semantic SEO:
- Internet Archive - Wayback Machine: This tool archives screenshots of websites from different time periods, allowing you to view historical versions of them. Access to archived versions of the website allows you to assess changes in its appearance and content, which is particularly important in the context of identifying unauthorized modifications that may indicate that the website has been taken over by third parties.
- Whois Lookup: Using Whois tools allows you to obtain information about a domain registration, including its owner and change history. Analyzing this data can reveal frequent changes in ownership, which could be a red flag for potential security issues.
- SEO tools like Ahrefs, SEMrush, Moz: These platforms offer backlink and website link profile analysis features, which can help identify unexpected or malicious inbound links that may have been added as a result of hacker attacks.
Why is checking the website history important?
Knowing the history of a website is essential to assessing its security because:
- Indicates Stability and Trustworthiness: A long-term online presence and a lack of negative security incidents can indicate that a website is solid and reliable.
- Reveals potential threats: A history of hacking attacks or data leaks indicates potential security weaknesses that may not be completely eliminated.
- Helps identify unauthorized changes: Regularly monitoring website changes can help you quickly detect and respond to unauthorized activity, protecting against malicious modifications.
Website Security Checklist
For everyone who has read the solid portion of knowledge from this article, I have prepared the following list of the most important security points.
- SSL/TLS Certificate: Make sure your website uses SSL/TLS encryption.
- Software Updates: Update CMS, plugins and scripts regularly.
- Strong Passwords: Use strong and unique passwords for all administrative accounts.
- Backups: Back up your website and database regularly.
- Web Application Firewall (WAF): Use a WAF or similar protection provided by your hosting provider
- Monitoring and Alerts: Set your site to be monitored for unauthorized changes and configure security alerts.
Implementing the points from this list does not provide 100% security, but it is a solid basis. Come back to it every month and check your penalty points and everything should be fine. Remember that security is a process and you cannot buy it once and make it last forever.
Frequently Asked Questions
What is an SSL certificate and why is it important for my website?
An SSL (Secure Sockets Layer) certificate is a standard security technology used to establish an encrypted connection between a server and a browser. This is a fundamental element in protecting data sent over the internet, ensuring that all data transferred between you and the website is secure and private.
How can I check if my website is secure?
To verify the security of your website, you can use website security tools such as Google Safe Browsing. Additionally, make sure your website's URL starts with "https://" and has a lock icon in the browser's address bar, which indicates the presence of an SSL certificate.
What is a DDoS attack and how can I protect my website?
A DDoS (Distributed Denial of Service) attack is a type of cyberattack during which a website is flooded with a huge amount of traffic generated by multiple sources, which may overload it and temporarily disable it. If you want to learn more, see the article about what is a ddos attack.
What are the best practices for securing a website?
Best practices for securing a website include regular software and plug-in updates, using strong passwords and multi-factor authentication, setting up a web application firewall (WAF), maintaining regular data backups, and educating users and employees on basic cybersecurity principles. If you want to know more about how to protect website against attack, check our other articles.
Are there tools that can help secure my website?
Yes, there are many tools and services that can help you secure your website. These tools include vulnerability scanners, content security management systems (CMS), identity and access management solutions, web application firewalls (WAFs), and security monitoring services. Remember, however, that the selection of appropriate tools depends on the specifics and needs of your website.

Adam Naworski